November 1, 2013
CryptoLocker malware spreading through campus, destroying data
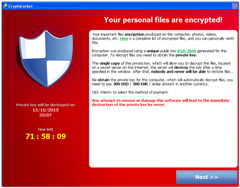
CryptoLocker is in a category of malware called ransomware. Once it's installed, it encrypts most of the files on your computer as well as any files stored on connected network volumes. The only way to recover the encrypted files is to pay a ransom to the criminals or restore from backups. Several instances of this malware have been reported on the K-State campus and some of them have encrypted shared network volumes, affecting entire departments and forcing administrators to perform large data restores.
All of the instances identified at K-State appear to have been spread via malicious emails appearing to come from "admin@ksu.edu" with subject lines like "Past Due Invoice." The email contains an attached zip file, which contains executable code that will install the malware. If you receive an email like this, please report it to abuse@k-state.edu and don't open the attachment.
 The office of information security and compliance is taking steps to reduce the threat, but here are some things you can do to ensure that you don't become a victim:
The office of information security and compliance is taking steps to reduce the threat, but here are some things you can do to ensure that you don't become a victim:
- Make sure your anti-virus software is installed and up-to-date
- Be extra cautious of emails with attachments that you weren't expecting
- Make sure important files are backed up
- Isolate your backups from your computer. If your backup method is an external drive attached to your computer, CryptoLocker could easily encrypt that data as well, so make sure to disconnect it when backups aren't running.
